Scan Maldoc
Document+PDF Malware Analysis
QuickSand Framework
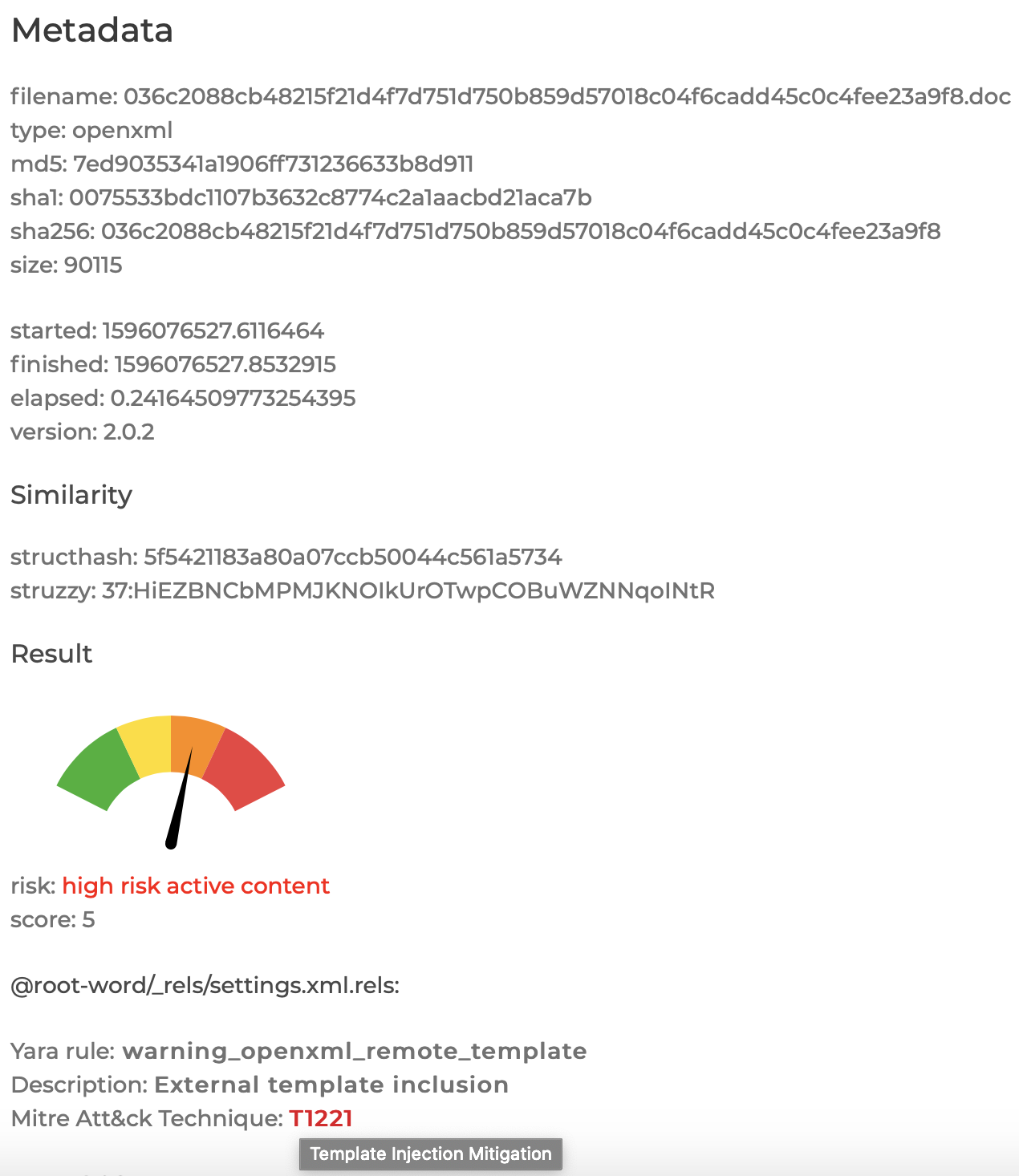
QuickSand is a Python-based analysis framework to analyze suspected malware documents to identify exploits in streams of different encodings or compressions. QuickSand supports documents, PDFs, Mime/Email, Postscript and other common formats. It is available for download github.com/tylabs/quicksand.
QuickSand supports scanning using Yara signatures within the decoded streams of documents and PDFs to identify exploits or high risk active content.
Features
-
Decode and decompress streams in OLE (Microsoft Word doc/Excel xls/Powerpoint ppt), OpenXML (Word docx/Excel xlsx/Powerpoint pptx), Hangul HWP, Adobe Reader PDF, Rich Text Format RTF, Postscript, Mime Emails, MSO, Adobe XML Data Package .XDP PDF. and Excel 4.0 Macros.
-
Scan with Yara within streams and sub-files.
-
Detect active content such as ActiveX, VBA, Macros, JavaScript, Shell commands.
-
Detect and define recent CVE IDs for known exploits.
-
Define Mitre Att&ck framework technique IDs for each exploit.
-
Handle nested formats, some encryption and nested encapsulation.
-
Open Source MIT License.